
If you manage a directory of users on your network outside of PerfectApps, you can use the synchronize option to dynamically update PerfectApps with the contents of your directory. Note that changes to users in PerfectApps cannot be migrated back to your directory at any point; synchronization is a one-way process. The PerfectApps system still maintains its database of users. Only a unique identifier (e.g., Distinguished Name or UID) is stored in its database for each user.
When users log in, their credentials are verified in the Directory Service. If the authentication is successful, the user is logged in based on mapping the single identifier. If the user does not already exist in the PerfectApps database, a new user is automatically created in the PerfectApps database; this means that every user in the Directory Service is automatically a PerfectApps user, even if there is no entry yet in the database.
 |
If you attempt to synchronize using a self-signed certificate the synchronization will fail. In these cases go to Account Settings and select the option to Ignore SSL certificate errors. |
|
To synch your directory to PerfectApps: |
1.Go to the Settings Dashboard. 2.In the tree, expand Account Settings > Users > Synchronize. 3.Configure the call to the directory service in the details area. Enter the directory service's host machine IP address, port, and other connection credentials. (** See Note below) 4.The synchronize feature supports use of SSL & Global Catalog. Check the Use SSL & Use Global Catalog checkbox to permit these features. (** See Note below) 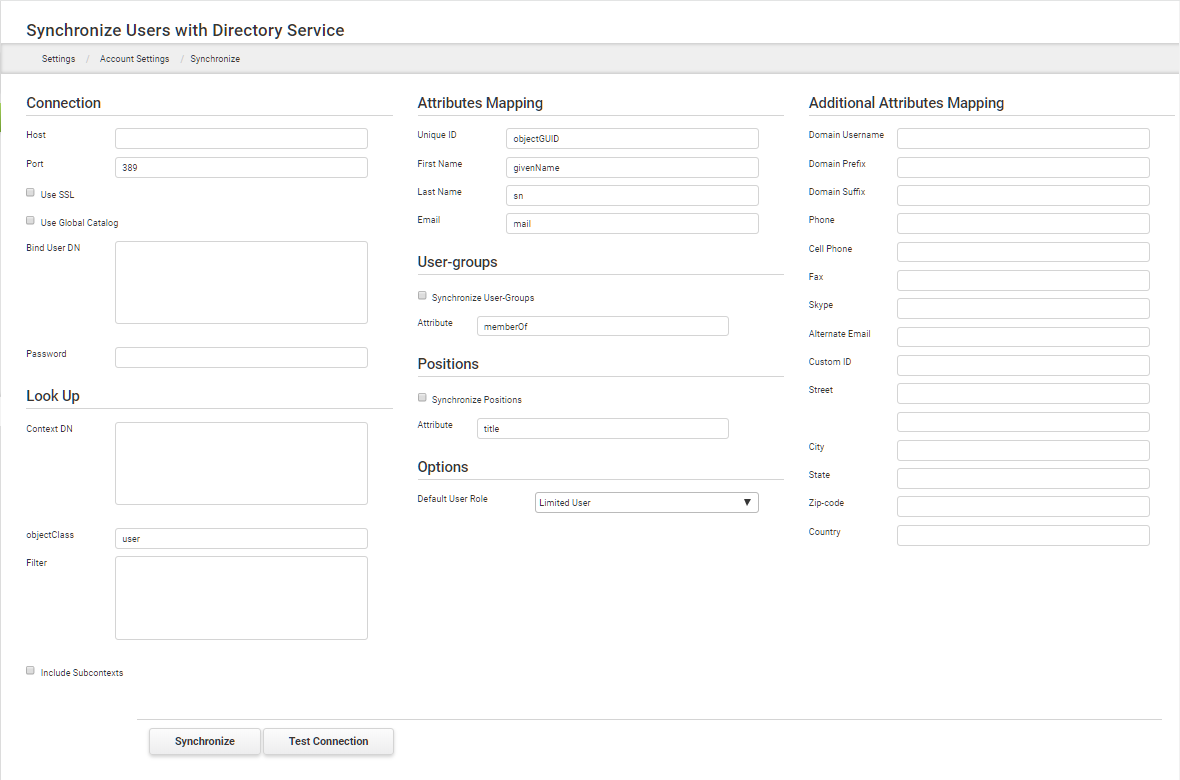
5.Enter the context distinguished name (Context DN) from Active Directory in the Look Up area. Optionally, specify a filter (for example, CN=a*, which only returns entries where the common name starts with 'a'). 6.Check the Include Subcontexts checkbox to allow reading of sublevel nodes inside the Active Directory environment. 7.In Attributes Mapping, sample attributes are supplied but you must enter the Unique ID attribute precisely as it appears in your active directory structure. The attribute name in your system is also needed for First Name, Last Name and Email (for example, userPrincipalName). 8.Optionally, you can automatically assign users to a user-group and/or position. Select the corresponding Synchronize check box under each section and enter the active directory attribute name that contains that information. 9.Optionally, assign a default log-in type. Limited User is selected by default since this option does not use a license. 10.Additional attributes can be mapped, including Domain Username, Phone, Custom ID and more.
11.Click Apply Changes. 12.Click Test Connection. If your connection is not successful, you may have entered incorrect information in the Connection area. Verify your Host IP, Port, and binding. |
||||
|
Return to: Administering Account Settings, Account Setup and Administration


